CVE-2024-9324 Exploitation Chain: Web User to NT AUTHORITY SYSTEM
Step by step exploitation for the Code Injection vulnerability that I found.
Hello everyone! Today I will present one of my first CVEs, which is very special to me. Although it is not considered highly critical, since it is a Reflected Cross-Site Scripting, this vulnerability, when combined with creativity, can provide very interesting results in real-world targeted attacks — even making it possible to control devices in homes.
Gira HomeServer is a home automation server from the German brand Gira. It works as the “brain” of a smart home connected via KNX (international standard for building automation). Through it, it is possible to integrate and control various systems and devices in a home or building, such as:
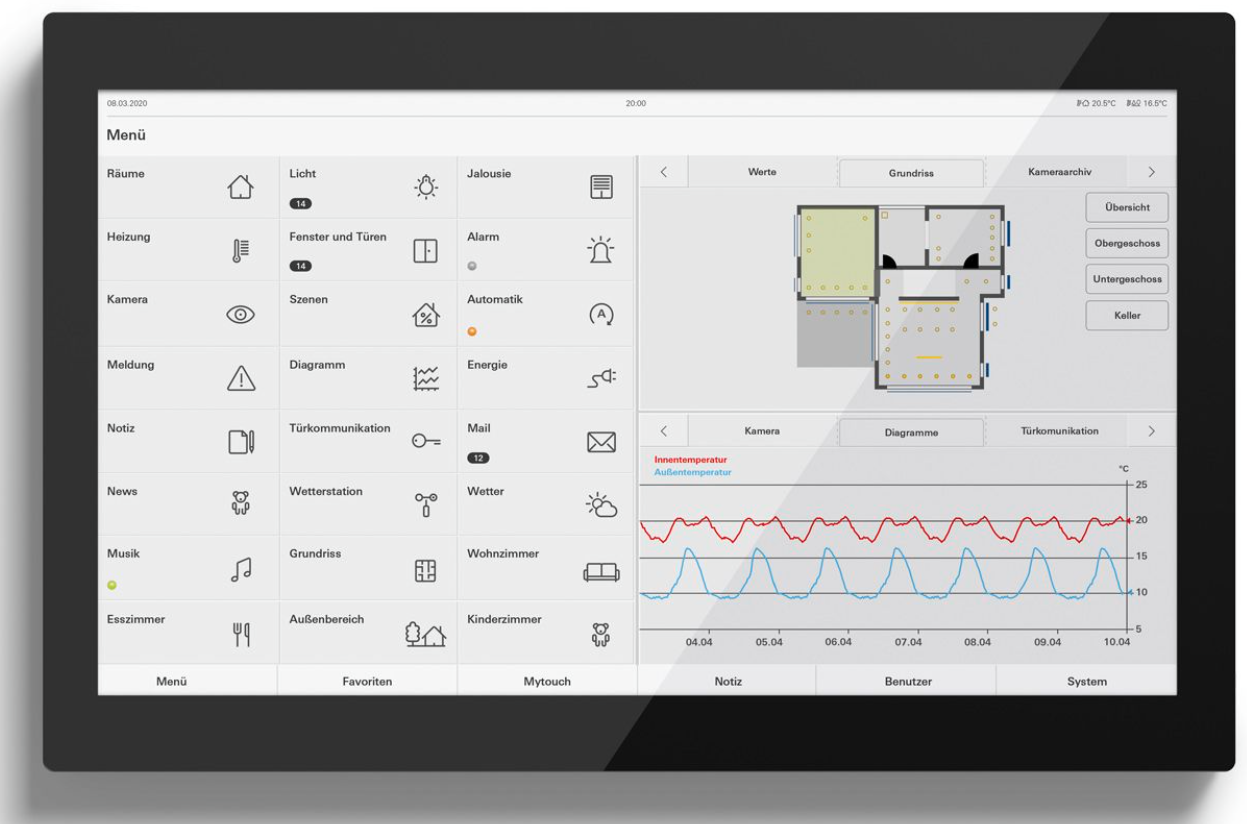
Gira HomeServer allows centralized management of these devices, facilitating the creation of personalized scenarios and remote control via smartphone, tablet or computer. This offers greater convenience, energy efficiency and security, in addition to enabling better use of building automation features.
But how did I find this vulnerability? I usually take the time to explore tools like Shodan and Fofa.io. I remember that one day I was mapping IoT technologies applied at scale when I ended up identifying a Gira HomeServer host.

The exploit is actually quite simple. In an unauthenticated manner, I was able to identify a vulnerable parameter that did not perform data sanitization correctly.
http://host.com/hslist?lst=debug"><img src=x onerror=alert(document.cookie)>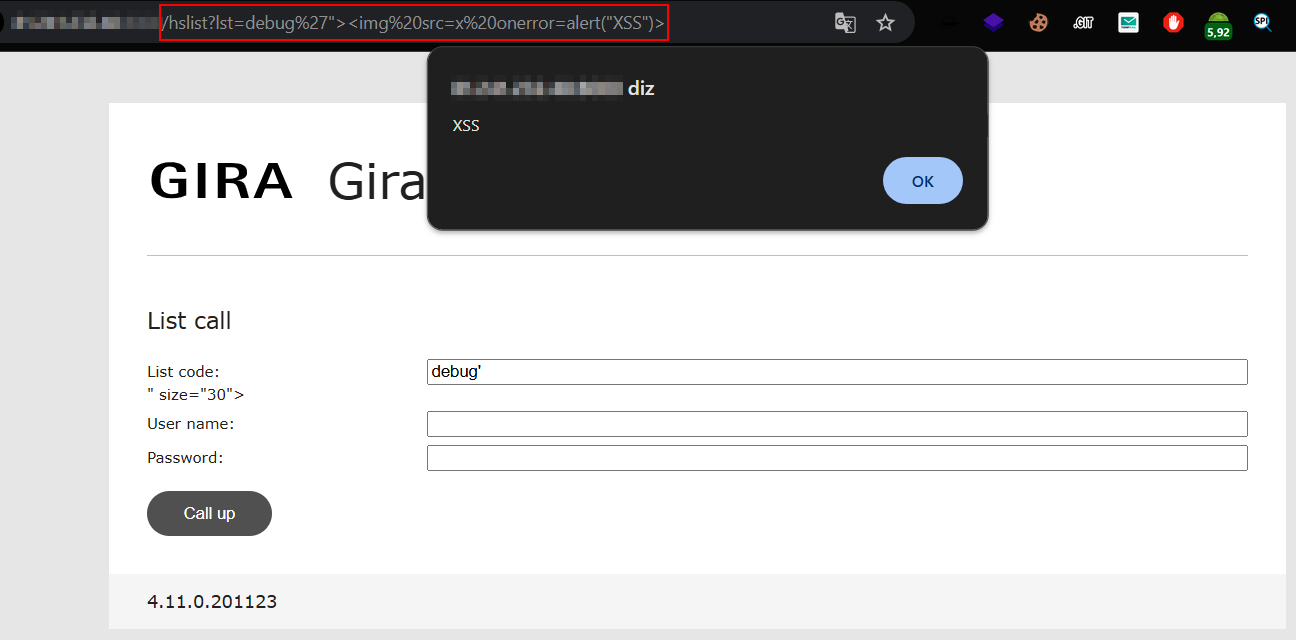
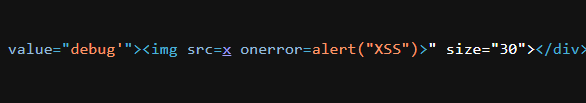
Great, we have an RXSS in the smart home management panel, how can we use this to our advantage?
In an operation in which our target uses a vulnerable device, we could create a trap through social engineering to induce them to perhaps click on a button that would execute a request to the page with cross-site scripting and end up stealing their session or directly executing actions in the application. Of course, this would generate a high level of exposure on the part of the attacker, so it would be necessary to understand the target, plan the attack, think of alternatives and, above all, protect yourself with OpSec. Each action needs to be carefully thought out, planned and reviewed, taking into account the most diverse factors. After all, we don’t want to throw the operation in the trash by causing a state of alert in the target. We can’t make them suspicious of anything. Anyway, I tried to give some insights on how this could be used. We always need to be creative in order to be able to chain strategies with vulnerabilities to achieve an objective. What if we could get the user’s session? Then we would have total control over the physical environment, locks, alarms, sensors, air conditioning systems… Wouldn’t it be amazing?
Well guys, this is the beginning of a long work that I am developing in Security Research. I recently started my studies in Assembly and IoT Hacking with the objective of acquiring products and carrying out research. Good posts with several insights should appear soon!
That’s it for today guys, I hope you enjoyed this vulnerability and don’t forget, keep hacking.
